According to myth, vampires can only enter your home if you let them in. Hackers, the vampires of cyber-world, are out there, waiting for you to ‘invite’ them in so they may feed on your private information.
There is no better time than cybersecurity month to strengthen your online login security protocols for the office and your personal accounts. Since the majority of information is stored electronically (rather than on paper), it can be accessed from almost anywhere in the world. However with that convenience comes risk, because anyone else in the world may potentially gain access to your information too! Yikes!
Below are simple steps you may take to protect yourself.
1. Never use the same password for multiple online accounts. It is imperative that each online account have a different password. Some companies own multiple online platforms, so if one website is hacked, the hacker may then have access to another account (or accounts). Depending on how many different accounts have the same password, instead of one compromised account, now you may have many.
2. Change your passwords often. Just because you don’t think you have been hacked does not mean you have not been hacked. An ideal attack takes time to develop. An intruder may obtain access to your account, then wait for several months before taking any action. Hackers can get into your account and study your behavior over time. They then know the perfect moment to strike.
3. Always confirm that there is a  “lock” icon on any website you log into. The lock icon shows the site is a secure website.
“lock” icon on any website you log into. The lock icon shows the site is a secure website.
In addition, any website that you enter sensitive information into should begin with “https” (note the “S” is for secure).If the site does not have https, leave the site immediately. It could be a spoofed site, one which tries to portray itself as a legitimate company’s site.
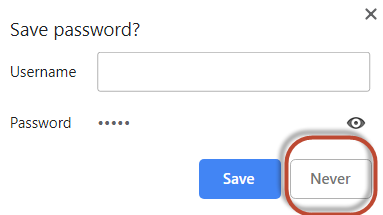
4. Never save your password within your internet browser. Yes, it is convenient, but it comes at a price. It may be your desktop computer, and yes, it is in your house or your office, but thieves have broken into offices and homes and stolen computers. Once that computer is out of your hands who knows who will have access to all your data. Don’t make it easy for them to gain access to your accounts.
5. Use strong, complex and long passwords. A pain, yes, but also a lifesaver. Make them at least 14 characters long, use numbers, and special characters. Make your password unique and do not use personal information. Everyone knows your dog’s name and everyone knows your favorite football team. There are numerous password-cracking tools out there - keep strong passwords to prevent those applications from figuring them out.
6. Whenever possible, use two-factor authentication. This a multi-step verification process which uses two different forms of identification to confirm it is you. The user has a password and is provided a code delivered in separate form. The second-factor code is for one-time use, and may be delivered using text messages, emails, biometrics, security keys, or tokens. Most sites are now implementing two-factor authentication. Always enable the strongest authentication options available.

7. Never keep the default password. Often when you create an online account, the site generates an easy non-secure password. Change it immediately! “Admin”, “1234”, “Hello”, “Welcome” are all easy to remember, but also easy for anyone to gain access to your accounts.

8. Pay attention to “last login” and set up alerts. For example, when you log into your email account, does it display the last time someone logged into this account? Was it you? This small step will inform you immediately if someone else has obtained access to your private account. Some accounts will send you a notification – via email, or text for example - each time someone logs in.
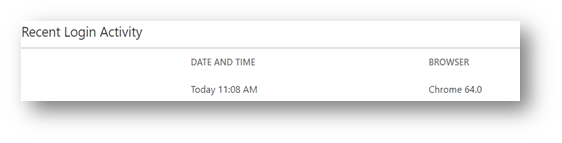
Realistically, a username and password just are not enough to guarantee the safety of your information. Banking and social media sites are the number one targets for hackers. If you have any online accounts of this nature, you already might be on someone’s target list.
With strong security settings in place, complex online passwords, and traceable logins, you can discourage the hacker. Be vigilant! Your accounts are vulnerable and the vampires are waiting.